Ledger Technology & Zero Knowledge Proof
Ledger technology is a system that records transactions in a way that's both verifiable and tamper-resistant. It operates as a decentralized system, which means it is not under the control of a single entity. This makes it perfect for documenting transactions that require transparency and strong security, such as financial transactions.
There are various types of ledger technology, but the most renowned one is blockchain. Blockchain is a form of decentralized ledger that employs cryptography to protect its data. This makes it exceptionally challenging to tamper with or hack.
Zero-knowledge proof is a cryptographic method that allows one party to demonstrate to another party that they possess a particular piece of information without revealing what that information is. This can be employed to confirm a person's identity or demonstrate access to a specific resource, all while keeping personal information undisclosed. Zero-knowledge proofs are often utilized alongside ledger technology to enhance the privacy and security of transactions.

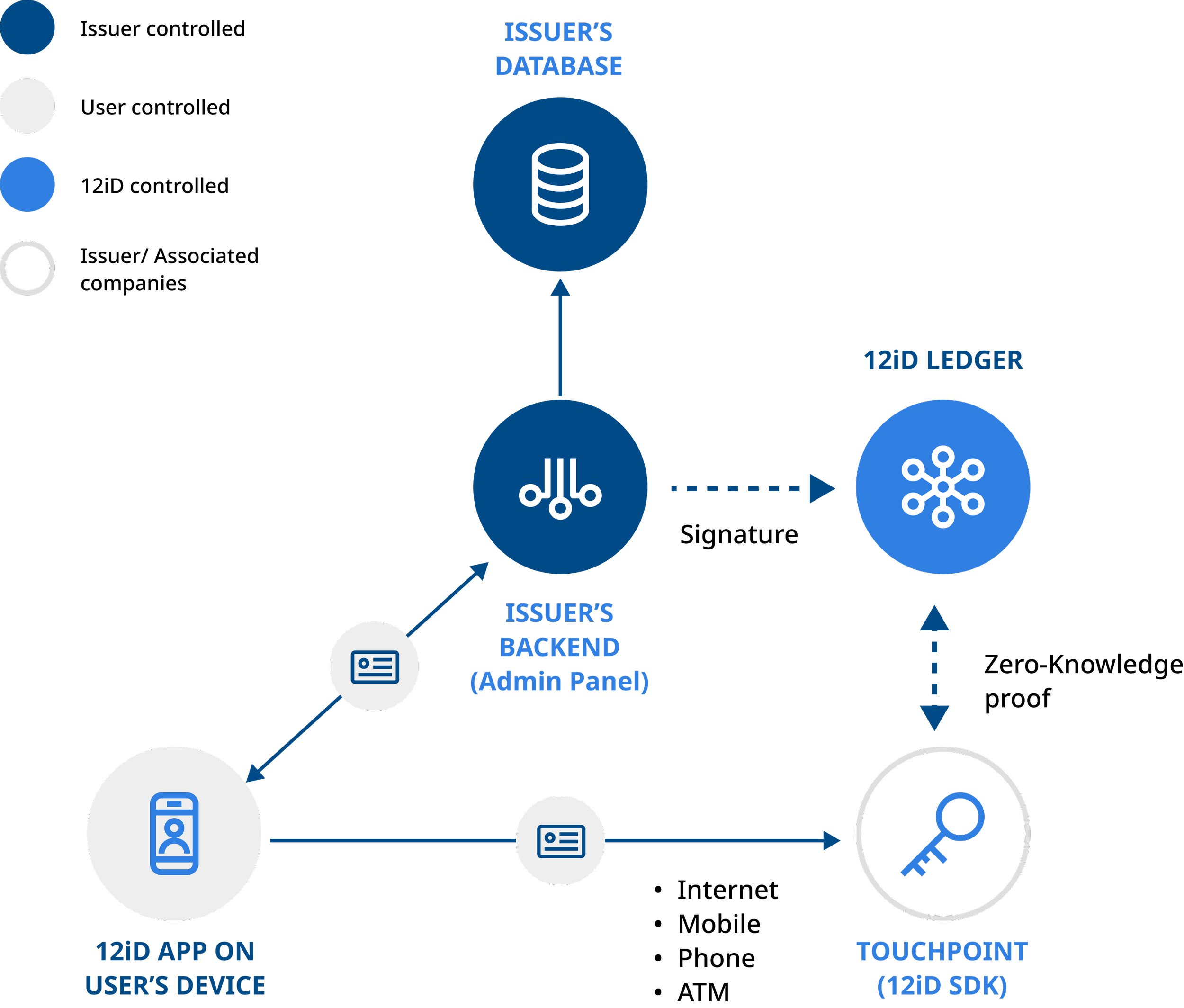
The 12iD data flow
12iD serves as a comprehensive solution for managing digital identities. It mainly consists of three key components: a user-friendly mobile application for end-users, an extensive admin panel for identity management, and an Identity Verifier service that relies on a private ledger to securely store identity provider signature data and identity revocation lists, ensuring the validation of data. Additionally, a set of connected touchpoints act as gateways for your web portals, mobile apps, or external devices like ATMs and check-in gates.
This system is not only secure but also easy to implement, offering a seamless user experience. Security is ingrained in the architecture through decentralized key management at its core, zero-knowledge proof, and trusted elliptic-curve cryptography to maintain confidentiality. It's important to note that no personal information is retained on the ledger,
Within the 12iD architecture, sensitive data is never shared with others. However, if the identity providers choose to trust each other, end-users can authenticate themselves with these trusted providers.
Live biometrics & Liveness check
Biometric Authentication uses unique characteristics from a person to confirm their identity. Most commonly, this involves device biometrics, where collected data is matched with pre-saved information on the device, FaceID on Apple or fingerprint on Android. However, device biometrics may not guarantee the person matches their claimed identity during a transaction.
To overcome this, 12id uses live biometrics. During a transaction, we collect real-time biometrics from the user and verify them against the stored data of the authorized user for that transaction. This ensures the person not only records their biometrics with us but also confirms their identity for the transaction.
Before collecting biometrics, it's crucial to verify the data comes from a genuine person and not a fake identity, using methods like screen recordings. At 12id, we achieve this through liveliness detection. This involves applying AI algorithms to various data sources, such as facial expressions and movement, to confirm authenticity and prevent fraud.
The Evolution of Digital ID
CREDENTIALS
(1995-2000)
Simple & cheap
Easy to hack
ID is not unique
Not user-friendly
TOKEN (OTP)
(2000-2005)
Add security
ID is not unique
Expensive
Not user-friendly
PKI-CERTIFICATES
(2005-Current)
Saas based
Vulnerable tech
Expensive integration
National only solution
WEB 3.0
Future
Saas based
Cost effective
Global solution
Unique identification
Key technical features
Compliance
Ensuring compliance with regulatory requirements is a top priority for us, and our solution is specifically designed to meet these requirements. It helps in establishing internal compliance necessities, allowing for detailed control over internal data visibility. Simultaneously, it helps fulfill external regulatory compliance while safeguarding the anonymity of end-users. It's worth noting that this aligns with our practice of not storing or sharing personal information between 12iD and the identity provider and associated companies.
Audit possibilities
You can easily export all your encrypted activities and share them with an authorized third party, like a government agency, to prevent fraud and corruption. The provided APIs also allow you to expand the solution, so we can help you address global data regulation concerns.
Scalability
Our decentralized and carefully designed architecture guarantees scalability across borders, enabling end-users to securely share data with their consent. We achieve this through cutting-edge algorithmic verification methods, delivering a swift, secure, and user-friendly experience, all while keeping dependencies minimal to avoid any data regulation complications.
Software updates
We use containerized services, making it simple to upgrade to the latest software versions. This ensures you get new features, bug fixes, and improved configurations hassle-free.
Our APIs make adding extra functions easy, allowing you to add more features to the Admin Panel by connecting it with other IT systems, databases, or services. This means you can expand the system beyond its original design while maintaining its strong core functionality.
Connect with APIs
Securing your data
We prioritize security with our unique architecture. It's built on distributed ledger technology (DLT), hashing technologies, Zero-Knowledge Proof (ZKP), and established elliptic-curve cryptography to ensure robust security. Our security features are embedded at every level of the solution, safeguarding communication channels on mobile devices and the verification process. We achieve this without relying on personal information, enhancing the overall security of your data.
Self-Sovereign Identity
We provide a Self-Sovereign Identity (SSI), granting individuals and organizations control over sharing their credentials and engaging on equal terms. Users can choose which parts of their credentials to share with each organization, putting them in control of their identity.
Phishing protection
Our authentication approach is mutual, verifying only valid requests from authorized sources and preventing forged companies from making requests. Our dedicated mobile app operates with minimal communication, allowing only end-to-end encrypted intents. This strategy markedly lowers the risk of phishing attacks and authentication fraud.
Smooth onboarding
Starting with our solution is effortless for both identity providers and associated companies. Our robust SDKs and APIs offer strong support, ensuring a seamless onboarding process.
Support
We focus on making the user experience a top priority in our front-end design and improvements. Both end-users and Admin Panel operators can expect a straightforward, user-friendly, and seamless experience. Tutorials will be provided during onboarding to ensure a smooth start.
Flexible data access control
Our Admin Panel gives identity providers the flexibility to set up user groups, controlling different data layers precisely. Data can be stored on-site or in the identity provider's cloud. This ensures compliance during identity processes, aids in monitoring the 12iD infrastructure, and allows access audits to prevent unauthorized entry.